|
Design
and technology
| 1. |
a) |
Imagine
Australia had a government that oppressed people
and you had to escape.
i) Where would you go?
ii) What country would you try to go to? |
|
b) |
| i) |
What
do you think would happen when you got there? |
| ii) |
Would
the people in the other country just let you
come in and do what you like? |
| iii) |
Or
would they want to know who you were and why
you wanted to be in their country? |
|
| |
c) |
What do you think it would be like to live in a
refugee camp?
See if you can find some information on the Internet
about life for refugees around the world. |
| 2. |
a) |
Imagine you work for the government and a lot of
refugees flooded into the country. Imagine you have
been asked to work out what to do with them, how
to look after them, how to keep track of them. |
| |
b) |
| i) |
How
would you organise dealing with them? |
| ii) |
How
would you decide who should be able to stay
in Australia and who didn't really need to
escape from their original country? |
|
| |
c) |
See if you can find some information on the Internet
about how the Australian Government looks after
refugees and how it decides who stays. |
| 3. |
a) |
Should technologies be used to identify and keep
track of people? Why? |
| |
b) |
If a technology exists, then it might be used for
controlling people. If the technology exists is
it always OK to use it with people? |
| 4. |
a) |
Do we have the right to keep things about ourselves
private? If we do, how can we control the way technology
is used to process and distribute information about
us? |
| |
b) |
Should
some technologies not be used for information systems
about people? Should it be allowed but should governments
regulate it? |
| 5. |
|
What if someone who has nothing to do with a crime
does not want to provide a sample for DNA identification?
Should you have the right to keep this information
private? Or, should you have to provide that information
about yourself, even if the police do not actually
suspect you in particular? |
| 6. |
a) |
Watch the sci-fi film Wedlock.
Identify the tagging mechanism used in the film.
|
| |
b) |
Compare
and contrast the identification and tracking system
used in the film with the DMPIT system using AVID
technology. |
| |
c) |
Identify
and discuss any ethical and social issues arising
from the type of control system used in the film. |
Information
processes and technology
Information systems
| 1. |
For the DMPIT system used at Guantanamo Bay, identify
and discuss:
- the
purpose of the system, including who it was
for and why there was a need
- the
data or information used in the system
- the
information technology used
- the
participants involved.
|
| 2. |
Distinguish
between, and categorise activities within the DMPIT
system in terms of the seven information processes. |
| 3. |
For the DMPIT system, diagrammatically represent
the information system.
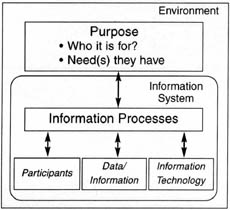
|
| 4. |
Explain how the need of the United States government
to gather information about refugees in camps was
supported by DMPITS. |
| 5. |
In the refugee camp at Guantanamo Bay, identify
the people who are:
- in
the environment
- users
of the DMPITS
- participants
in the information system.
|
| 6. |
Use a data dictionary to describe the data collected
on the refugees. |
| 7. |
Identify the data in the DMPIT system and the information
that it is transformed into. |
| 8. |
Describe
how the data used by the DMPIT system is digitised
by the hardware that collects it. |
| 9. |
Draw a data flow diagram to illustrate the data
flow in the DMPIT system. |
Social
and ethical issues
| 1. |
Identify
the privacy implications to individuals subjected
to the DMPIT system employed to keep track of refugees.
Propose strategies to ensure the human rights of
individuals are protected. |
| 2. |
Identify and discuss issues of access to, and the
control of information contained in DMPIT systems
operated by governments. |
| 3. |
Discuss the social and ethical issues of organisations
using DMPITS to keep track of their employees. |
Related
systems
| 1. |
Local councils have information systems for pets,
to keep track of all dogs and cats, through the
use of microchips which are inserted under the
skin of the pet. This enables councils to identify
if a cat or dog is either a stray or a pet, and
then locate and return it to the owners.
For a pet information system:
- Identify
and describe the required information technology,
participants and data or information.
- Create
an appropriate data dictionary to describe the
data which would assist councils in returning
lost pets to owners.
- Describe
the social and ethical issues associated with
this system, including issues associated with
incorrect data.
|
| 2. |
A government wishes to keep track of its soldiers
going on a tour of duty to a foreign country. Identify
and describe the information processes and information
technology required to develop such a system. Identify
and discuss any security, access or control issues
of this system. |
Research
Software
design and development
Increasing levels of technology can either provide centralised
control systems which concentrate power in the hands
of fewer and fewer people, or distributed systems which
place some control with many individual users, for example,
the Internet.
Discuss
the implications of emerging information control technologies
on the future of democratic societies.
References
American Bible Society (1976) Good News Bible,
American Bible Society, New York, p. 315.
Beniger, J. R. (1986) The Control Revolution, Harvard
university Press, Massachussetts, p. 39-40.
Brady, T. V. (1998) The IDENT System: "Putting
Structure to the Chaos of the Border", National
Institute of Justice Journal, 237, October 1998.
http://www.ncjrs.org/txtfiles/jr000237.txt
Brakeman, L. (1994) New DoD system tracks refugees,
Automatic ID News, Vol 10, No 13, pp. 1, 14-17.
Advanstar Communications Inc.
Dechman, G. H. (1996) Fingerprint Case Study: The Haitians
at Guantanamo Bay, DMPITS Case History, http://www.fpusa.com/pubs.htm
Global Supermarket (2002) Technology to the test, Global
Supermarket: Official publication of the National Food
Industry Strategy, Global Supermarket, Vol, 6, No.
2, p. 53. http://www.globalsupermarket.com.au.
Masland, T. et al (1994) A US invasion of Haiti?, Special
Report for Newsweek, The Bulletin, July 19, pp. 58-63.
Powerhouse Museum (2001) Cyberworlds:
computers and connections, Powerhouse Museum,
Sydney, p. 9.
|