|
Deployable
Mass Population Identification and Tracking System (DMPITS),
is a very sophisticated information system. It's a way
of identifying large numbers of people, and storing
information about each of them.
It's
deployable because it can be set up wherever it's needed.
Different workstations are used to check the identity
of people, or to make new entries on a centralised database.

Chief Richard Read and Captain Veronica
Lussio, USN, inspect DMPITS equipment still stored
in specially designed shipping cases, ready for
deployment. Photo: Lynne Brakeman.
|
DMPITS
was originally developed by the US armed forces to help
them deal with thousands of refugees
who ended up in refugee camps controlled by the United
States military. They wanted to set up an information
system that would let them keep track of exactly who
each one of the refugees was, and store information
about each of them. They wanted it to be foolproof,
so everyone would always be in exactly the right place
in the information system.
The
system they set up uses three different ways to identify
people:
- what
they look like
- their
fingerprint
- an
identification number.

This MP works in the DMPITS station
under the tents in a Haitian camp. Photo: Lynne
Brakeman. |
The
process
- When
a person first gets entered into the system, they
are enrolled at one of the workstations.

A soldier escorts a refugee to the
workstation. Photo: Lynne Brakeman. |
- First
they put their finger on a glowing red fingerprint
scanner. This reads their fingerprint and converts
it into a digital form. Then the entire database is
checked to make sure they don't already have a file.
If they don't, a new file is created and their fingerprint
entered.

Glowing red fingerprint scanner.
Photo: Lynne Brakeman. |

A soldier guides a Cuban refugee's
hand to ensure a quality fingerprint scan. Photo:
Lynne Brakeman. |
- Next
they have a black plastic wristband placed around
their wrist and secured with a rivet, or if they're
a very small child, around their ankle. The wristband
contains a read-only microchip with a unique nine
digit number. An AVID scanner is used to read the
number on the wristband, and the number is entered
into the person's file.

The
pop riveter looks like a drill, but it painlessly
secures the wristband. Photo: Lynne Brakeman.
|

Close-up
of the wristband. Powerhouse Museum collection.
|
- Then
a video camera is used to film the person's face.
This image is also entered into their file.

A video camera is used to film the
person's face. Photo: Lynne Brakeman. |
- After
that, the person is interviewed, and information is
entered in their file about their name, date of birth,
age, sex, place of birth, nationality and so on.

Data
is entered on the computer. Photo: Lynne Brakeman. |
After
they've been enrolled in the system, their identity
can be checked any time by scanning their ID wristband.
To double check, they can be fingerscanned again to
make sure the fingerprint matches up with the ID number
in the wristband, and their video image can be brought
up on the screen to check that too.

RF/ID
scanners bridge the language barrier and provide
quick, positive ID. Photo: Lynne Brakeman. |
This
can be used to double check someone's identity. It can
also be used to identify someone who has taken their
wristband off and doesn't want to be identified.
Check
out the DMPITS
maker's website.
US
Immigration and Naturalization Service
When the US military used DMPITS to control the refugee
crisis they found that it worked really well. It did
the job so well that the US Immigration and Naturalization
Service (INS) adopted a version of it for their own
use. The INS is responsible for deciding who can get
into the USA and who can't, and keeping illegal immigrants
out. Because the USA has a land border with Mexico,
it's hard to stop people entering the country illegally.
The
INS adopted a version of DMPITS, and they renamed it
IDENT. There's no wristband or microchip, but the fingerscan
and video image are used. Every time they catch someone
trying to cross illegally into the USA, they fingerscan
them. If it's their first time, the INS creates a file
on them with their picture and fingerprint. After that,
the authorities can see how many times that person has
tried to get in, and where they've tried. This gives
the INS a lot more information than they've ever had
before, and that means they have much more power to
control illegal immigration.
Click
here to find out more about IDENT.
Information
systems like DMPITS and IDENT are very good at controlling
information about people. For that reason we can be
sure that as time passes more and more government bodies
around the world will start using information technology
like this to control what goes on.
Other
uses for DMPITS
The people who make DMPITS see all sorts of applications
for their information system. They suggest it could
be used to check eligibility for government welfare
benefits (like Austudy) or medical benefits (like Medicare):
- check
applicants for commercial driver's licenses
- monitor
prisoners or people on parole or bail.
Systems
like DMPITS and IDENT aren't used for these purposes
in Australia yet, but it's possible they could be in
the future.
DMPITS tech specs
DMPITS uses a group of high-performance computer workstations
joined together in a local area network (LAN). The hardware
devices are normal commercially available components.
System
server
The system server is a Hewlett-Packard 735 workstation
with:
- 80
megabytes of RAM and 525 gigabyte external hard drive
- 9.6
kilobyte per second analogue communications modem
- flatbed
scanner
- Hewlett-Packard
Laserjet printer with 6 megabytes of memory
- V42
modem.
Workstation
Each workstation is a Hewlett-Packard 715 UNIX workstation
with:
- 2
gigabyte internal hard drive
- 19
inch colour monitor
- keyboard,
and mouse
- Identix
TY-555 Touchview Fingerprint Scanner
- AVID
RF-ID scanner for inputting ID numbers from wristbands
or identity cards
- Panasonic
CCD colour video camera.
The
workstations run specially designed UNIX-based software,
including Automated Fingerprint Identification System
for reading and storing digital versions of fingerprints.
Here's
what it looks like:
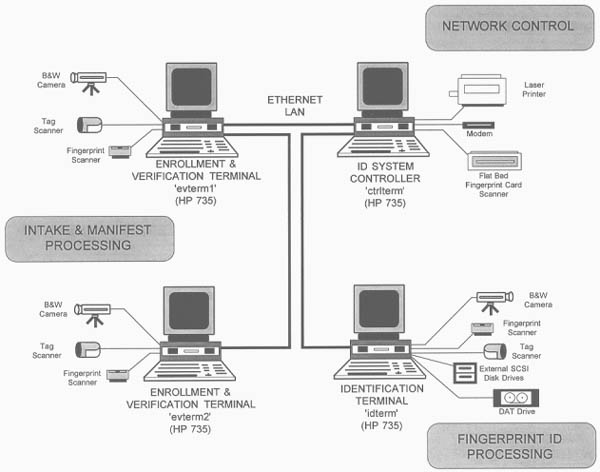
DMPITS architecture (Dechman, 1996:
1)
This
diagram comes from an article by Gordon H. Dechman (the
head of the company that designed DMPITS). You can find
the article at DMPITS
Case History.
Activity
Discuss issues of access to and control of information
raised in this case study.
|